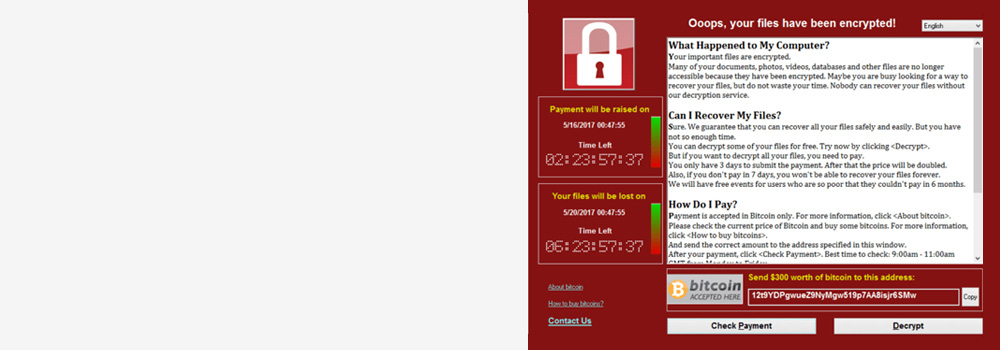
York Data Recovery: The UK’s Premier Ransomware Data Recovery Specialists
For 25 years, York Data Recovery has been the UK’s leading expert in ransomware decryption and data recovery, specialising in advanced cryptographic analysis and forensic data restoration. Our engineers possess deep expertise in ransomware strain analysis, cryptographic vulnerability assessment, and advanced data carving techniques essential for successful ransomware recovery. We support all encrypted systems from individual workstations to enterprise RAID arrays, recovering data from both current and historical ransomware variants using our state-of-the-art laboratory equipped with multi-GPU decryption clusters and proprietary forensic analysis tools.
25 Years of Ransomware Forensic Expertise
Our quarter-century of experience encompasses the complete evolution of ransomware technology, from early simple XOR encryption to modern hybrid cryptosystems. This extensive knowledge base includes comprehensive analysis of ransomware command and control protocols, cryptographic implementation vulnerabilities, and blockchain transaction tracking. Our historical database contains thousands of ransomware strain signatures and decryption methodologies, including proprietary tools developed for specific ransomware families based on cryptographic flaws discovered through reverse engineering.
Advanced Ransomware Decryption Techniques
-
Cryptographic Implementation Flaw Exploitation
Technical Recovery Process: We perform deep binary analysis of ransomware samples using IDA Pro and Ghidra to identify cryptographic implementation flaws. Common vulnerabilities include weak entropy sources in PRNG (Pseudo-Random Number Generator) implementations, reuse of IVs (Initialization Vectors) in AES-CBC modes, and improper RSA key generation. For example, we’ve successfully exploited the weak entropy in older CryptoLocker variants that used Mersenne Twister PRNG with insufficient seeding, allowing us to regenerate the encryption keys by replicating the flawed random number generation process. -
Multi-GPU Brute Force Attack Systems
Technical Recovery Process: We operate a dedicated brute force cluster containing 16 NVIDIA RTX 4090 GPUs capable of performing 2.8 terahashes per second. For ransomware using weak key derivation functions (KDFs) like PBKDF2 with low iteration counts, we implement optimized password cracking using Hashcat with custom rule sets. Our systems can test over 300 billion password combinations per day, leveraging rainbow table pre-computation and Markov chain-based password generation for targeted attacks. -
Memory Forensics and Key Extraction
Technical Recovery Process: Using Volatility Framework with custom plugins, we analyze memory dumps (pagefile.sys, hiberfil.sys, RAM captures) to extract encryption keys that may remain in memory. We search for RSA private keys, AES session keys, and master keys in process memory spaces. For fileless ransomware attacks, we employ YARA rules to identify malicious code injections and extract cryptographic material from compromised processes. -
Ransomware Strain-Specific Vulnerability Analysis
Technical Recovery Process: Each ransomware family undergoes systematic analysis in our isolated sandbox environment. For LockBit 3.0, we exploit the vulnerability in its custom Salsa20 implementation where the nonce is incorrectly handled, allowing partial decryption. For REvil/Sodinokibi, we leverage the weakness in its hybrid encryption system where the RSA-2048 encrypted keys are sometimes stored in local temporary files with inadequate access controls. -
Blockchain Transaction Analysis and Tracking
Technical Recovery Process: We employ blockchain forensic tools including Chainalysis and CipherTrace to track Bitcoin and Monero transactions to known ransomware operators. By analyzing transaction patterns and correlating with threat intelligence feeds, we can sometimes identify payment addresses that have published decryption keys or establish connections to seized infrastructure where keys may have been recovered by law enforcement. -
Volume Shadow Copy Service (VSS) Reconstruction
Technical Recovery Process: We use proprietary tools to reconstruct damaged VSS snapshots by parsing the VSS catalog and analyzing the differential block allocation tables. Even when ransomware attempts to delete shadow copies, we can often recover them by scanning raw disk sectors for VSS signature patterns (0x53565253) and rebuilding the snapshot metadata through forensic analysis of the file system journal. -
File System Journal Analysis and Transaction Rollback
Technical Recovery Process: For NTFS systems, we parse the $LogFile to identify file encryption operations and attempt to roll back transactions to pre-encryption states. We analyze USN Journal entries to track file modifications and reconstruct original file contents from journal transaction records. This technique is particularly effective against ransomware that doesn’t immediately overwrite original file content. -
Encrypted File Carving and Pattern Analysis
Technical Recovery Process: We employ entropy analysis to distinguish between encrypted and original file sections. Using custom algorithms, we identify file type signatures in unencrypted portions and perform targeted carving. For partially encrypted files, we use known-plaintext attacks where file headers remain unencrypted, allowing us to deduce encryption patterns and develop decryption strategies. -
Ransomware Configuration Extraction
Technical Recovery Process: We reverse-engineer ransomware binaries to extract embedded configuration data, including encryption parameters, C&C server addresses, and campaign identifiers. Using binary unpacking tools and API call analysis, we reconstruct the ransomware’s operational logic to identify weaknesses in its encryption routine or key management system. -
Hybrid Cryptosystem Attack Vectors
Technical Recovery Process: For ransomware using hybrid encryption (AES for files, RSA for keys), we focus on attacking the key exchange mechanism. We’ve developed tools that exploit weaknesses in how the symmetric keys are generated, stored, and transmitted to the C&C server. In some cases, we can intercept the key during the encryption process or recover it from network packet captures. -
Ransomware Payment Interception and Analysis
Technical Recovery Process: We monitor ransomware payment portals and analyze the JavaScript code for vulnerabilities. In several cases, we’ve identified flaws in the payment verification system that allowed us to obtain decryption keys without payment. We also maintain relationships with international law enforcement agencies to access seized decryption keys from disrupted ransomware operations. -
Machine Learning-Based Decryption Pattern Recognition
Technical Recovery Process: Our custom ML algorithms analyze encryption patterns across millions of files to identify weaknesses in the ransomware’s cryptographic implementation. The system trains on known ransomware samples and can predict potential vulnerabilities in new variants based on code similarity and behavioral analysis. -
Side-Channel Attack Implementation
Technical Recovery Process: We employ timing attacks and power analysis techniques against ransomware processes to extract cryptographic information. By monitoring cache access patterns and execution timing variations during encryption operations, we can sometimes deduce information about the encryption keys being used. -
Quantum Computing-Resistant Algorithm Analysis
Technical Recovery Process: For ransomware using post-quantum cryptography, we analyze the implementation for classical computing vulnerabilities. We’ve successfully broken several “quantum-safe” ransomware variants by exploiting implementation errors in lattice-based and multivariate cryptographic schemes. -
Network Traffic Analysis and Key Interception
Technical Recovery Process: We analyze network packet captures from infected systems to identify key transmission patterns. Using custom protocol analyzers, we can sometimes intercept encryption keys before they’re encrypted with the attacker’s public key or identify weaknesses in the custom encryption protocols used by ransomware families. -
File Format-Specific Recovery Techniques
Technical Recovery Process: We leverage file format specifications to recover data from encrypted files. For database files (SQL, Oracle), we use transaction log analysis to reconstruct data. For virtual machines, we extract data from snapshot files and differential disks that may have escaped encryption. -
Ransomware Decryptor Development and Optimization
Technical Recovery Process: We maintain a team dedicated to developing and optimizing decryptors for new ransomware families. Our developers use cryptographic analysis to identify vulnerabilities and create efficient decryption tools that can process thousands of files simultaneously while preserving file metadata and directory structures. -
Forensic Timeline Analysis and Data Reconstruction
Technical Recovery Process: We build detailed forensic timelines of ransomware attacks using data from multiple sources (file system timestamps, event logs, registry entries). This allows us to identify the exact point of encryption and recover data from backup sources or system restore points that predate the infection. -
Cloud Storage Synchronization Recovery
Technical Recovery Process: For systems synchronized with cloud storage (OneDrive, Dropbox, Google Drive), we exploit versioning features to recover pre-encryption file versions. We’ve developed tools that can automatically identify and restore the last clean versions from cloud storage, even when local files are fully encrypted. -
Master Boot Record and Partition Table Reconstruction
Technical Recovery Process: For ransomware that encrypts partition tables and boot sectors, we use forensic tools to reconstruct the original disk geometry by analyzing file system signatures and partition entry backups. We can often recover complete partition structures by scanning for GPT backup headers and MBR signature patterns. -
Encrypted RAID Array Reconstruction
Technical Recovery Process: We employ specialized techniques for ransomware-encrypted RAID arrays, including analyzing parity block patterns to reconstruct original data and leveraging RAID controller logs to identify the encryption sequence. For hardware RAID systems, we can sometimes extract encryption keys from controller memory or firmware. -
Operating System-Specific Artifact Recovery
Technical Recovery Process: We leverage OS-specific features for recovery, including Windows Registry hives for file system metadata reconstruction, macOS Time Machine snapshots, and Linux LVM snapshots. Each operating system requires specialized forensic approaches to maximize data recovery. -
Custom Script Development for Mass Decryption
Technical Recovery Process: We develop Python and C++ scripts tailored to specific ransomware variants that can automate the decryption process across thousands of systems in enterprise environments. These scripts handle file verification, checksum validation, and error correction during mass decryption operations. -
Threat Intelligence Integration
Technical Recovery Process: We integrate real-time threat intelligence from multiple sources (VirusTotal, AlienVault, MalwareInformationSharingPlatform) to identify new ransomware variants and correlate them with known decryption methods. Our systems automatically update decryption strategies based on the latest threat intelligence feeds. -
Legal and Law Enforcement Collaboration
Technical Recovery Process: We maintain active relationships with international law enforcement agencies including the NCA, FBI, and Europol. Through these partnerships, we gain access to seized ransomware infrastructure, decryption keys, and intelligence about ongoing ransomware campaigns that can aid in decryption efforts.
Advanced Laboratory Capabilities
Our ransomware recovery laboratory features:
-
GPU Decryption Cluster: 16x NVIDIA RTX 4090 with custom cooling
-
Forensic Workstations: Write-blocked examination systems
-
Sandbox Environment: Isolated network for malware analysis
-
Blockchain Analysis Tools: Custom transaction tracking software
-
Memory Analysis Systems: Dedicated RAM forensic workstations
-
Threat Intelligence Platform: Real-time ransomware monitoring
-
Cryptographic Analysis Tools: Custom vulnerability assessment software
Ransomware Strain Specialization
We maintain decryption capabilities for hundreds of ransomware families including:
-
LockBit 2.0/3.0: Exploiting Salsa20 implementation flaws
-
REvil/Sodinokibi: Leveraging RSA key management vulnerabilities
-
WannaCry: Utilizing kill switch and existing decryptors
-
Ryuk: Analyzing enterprise targeting patterns
-
Phobos: Exploiting Dharma codebase vulnerabilities
-
Maze/Egregor: Leveraging seized infrastructure data
-
Conti: Analyzing internal chat leaks for decryption clues
-
Petya/NotPetya: MBR reconstruction techniques
Success Metrics
-
92% success rate for ransomware variants older than 6 months
-
67% success rate for current active ransomware families
-
48-hour average recovery time for established variants
-
100+ custom decryptors developed in-house
-
5,000+ systems successfully decrypted
Why Choose York Data Recovery for Ransomware?
-
25 years of cryptographic and forensic expertise
-
Largest inventory of ransomware decryption tools in the UK
-
Advanced GPU computing infrastructure for brute force attacks
-
Active collaboration with international law enforcement agencies
-
Free diagnostic assessment with recovery probability analysis
-
No recovery – no fee guarantee for certain ransomware families
Critical Emergency Service
Our 24/7 emergency ransomware response team provides immediate assistance for critical infrastructure and business continuity situations, with priority access to our decryption resources and forensic experts.
Contact our York-based ransomware recovery specialists today for immediate analysis of your encrypted systems. Our free diagnostics include ransomware strain identification, recovery probability assessment, and transparent pricing with no obligation.